The Sudo program is used to secure your SSH client and, for example, counteract intrusion. Below we describe how to manage users of the SSH client.
Creating a new user
In the following example, we have chosen to use the Loopia support username, but you can of course choose something else. Enter the following command:

Please choose a personal username that is not associated with the company, and avoid “common” usernames such as admin, as intrusion attempts with these are also common. When you run the command, you can choose a password and fill in a few other tasks. Of these, only the password is important, the rest you can leave blank if you want. Keep in mind that the username, like everything else in most Unix environments, is case sensitive; “Loopia Support” is not the same as “loopia support”.
Give the user temporary administrative rights
The user you just created has no rights to run any commands. Giving a user the ability to run any command, at any time, is a huge security risk. Therefore, we will use sudo. sudo is used to give the user temporary administrative rights.
To run a command with administrative privileges, simply type sudo before the command you want to run, such as sudo apt-get update.
We give a user sudo rights with the following command:

This command adds the user loopia support to the sudo group. All users in the sudo group have full access to using the command.
An alternative method of giving the user sudo rights is through the visudo command. If you run visudo, a text file will open that includes a line that looks like this:

Copy the entire line and paste just below, but replace root with your username:
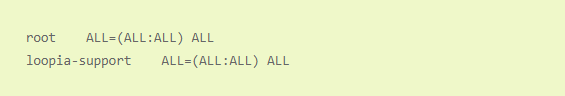
When you save this file, the user will be able to use sudo. To test it you can switch to your new user using the su loopia support command. Of course, you change “loopia support” with the username you have chosen. Because you are logged in as root when you run this command, you do not need to enter a password, but you will be able to log in directly as the new user.
Authenticate the user to run sudo
To run sudo, you must authenticate yourself by entering the user password. Once you’ve done that, you will remain authenticated for five minutes. During this period, you still need to use sudo, but you do not have to enter the password for each command. It is often called “run a command as root”, even though it is not the username root used when administrative rights are required. For simplicity, we will use that phrase from time to time in these instructions.
If everything seems to work properly, close the connection to your VPS and connect again with your new username instead.
Turn off the ability to log in as root
We mentioned earlier that over 98% of SSH intrusion attempts occur with the username root, so a very simple method of protecting against these intrusion is to turn off the ability to log in as root.
We do this by editing the /etc/ssh/sshd_config file. If you followed our instructions until the letter you probably have no simple editor installed so we recommend that you install the nano software which is a very simple editor. Then edit the file with the following command:

Look up this line:

Here you simply change “yes” to “no“.
By default, SSH is used on port 22. To increase security even more, you can replace it with something else by changing the line “Port 22” to any port between “1-65535“. However, you should choose a fairly high number to reduce the risk of colliding with another port that you may use later.
Then save the file and close. In nano, you do this by pressing Ctrl + X. If you have changed anything, the program will ask if you want to save the changes. Answer yes by pressing “y” and then press “enter“. In order for our new settings to take effect, you need to reboot the SSH server:

When someone is now trying to log in as root via SSH then they will receive an error saying that the login failed as if they had entered an incorrect password. If you have changed SSH port, you will need to manually enter this in the future when you connect to your server.
Tip! If you happen to lock yourself out, you can still log in as root via the Screen Console that you find in your Loopia Customer zone now that it does not connect via SSH.